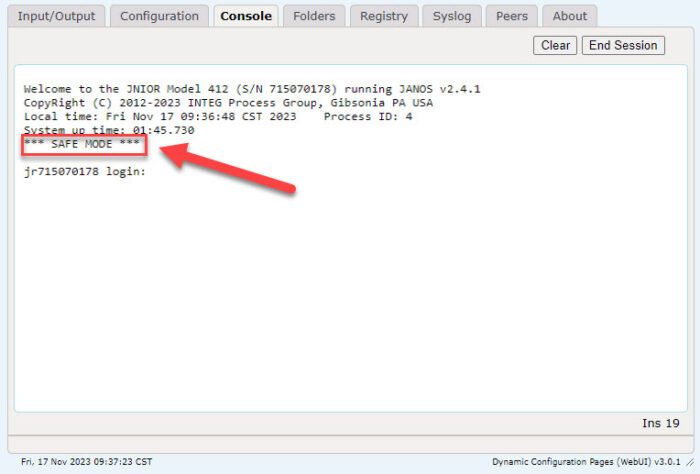
In the Programming Tips I show you how to make an outgoing secure connection using SSS/TLSv1.2. A secure connection encrypts data with a 128-bit key that is itself securely negotiated. So the information that you exchange cannot be read from the wire as it passes. But Windows still says “Not Secure” sometimes. Why is that?
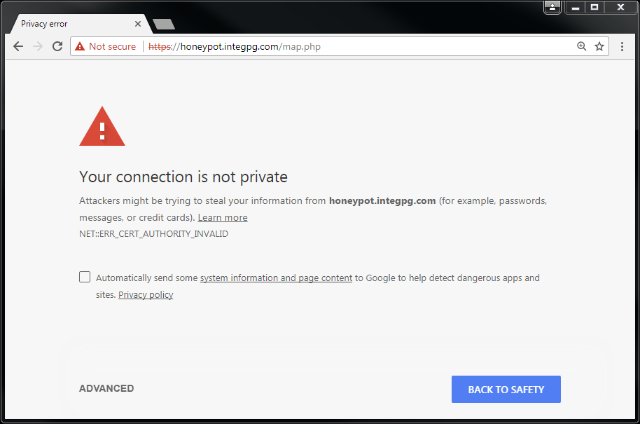
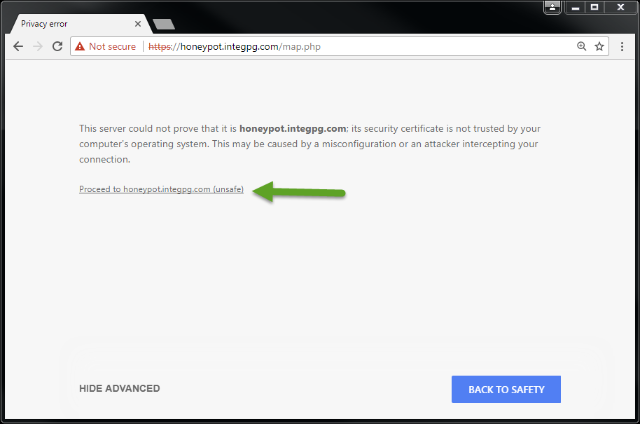
By “Not Secure” Windows is really telling you that the connection is Not Trusted. The data is still encrypted but Windows doesn’t recognize the connected client. If you have connected to a JNIOR using the HTTPS URL before you might heave seen a Privacy Error page that you must bypass in order to access the unit. This occurs as the browser receives a certificate from the JNIOR which is not traceable through a Root Certificate Authority in its database. The JNIOR certificates are self-signed and not issued by such an authority. Ergo the privacy concern.
When your application makes an outgoing connection the destination sends a copy of its certificate. Can you verify that certificate as the browser does? Well, with limitations you can. I have added a method in the Socket class allowing you to retrieve that certificate.
Once you indicate that the connection should be secure there is a brief period in which the negotiations transpire. The following code waits for a certificate. The getCertificate() method returns an empty byte array until a certificate has been received.
bruce_dev /> jtest
30 82 02 ed 30 82 02 56-a0 03 02 01 02 02 04 24 0...0..V .......$
99 a9 00 30 0d 06 09 2a-86 48 86 f7 0d 01 01 0b ...0...* .H......
05 00 30 81 81 31 20 30-1e 06 03 55 04 0a 0c 17 ..0..1.0 ...U....
49 4e 54 45 47 20 50 72-6f 63 65 73 73 20 47 72 INTEG.Pr ocess.Gr
6f 75 70 20 49 6e 63 31-17 30 15 06 03 55 04 0b oup.Inc1 .0...U..
0c 0e 4a 4e 49 4f 52 20-43 6f 6e 74 72 6f 6c 73 ..JNIOR. Controls
31 1d 30 1b 06 03 55 04-03 0c 14 68 6f 6e 65 79 1.0...U. ...honey
70 6f 74 2e 69 6e 74 65-67 70 67 2e 63 6f 6d 31 pot.inte gpg.com1
25 30 23 06 09 2a 86 48-86 f7 0d 01 09 01 16 16 %0#..*.H ........
62 63 6c 6f 75 74 69 65-72 32 40 63 6f 6d 63 61 bcloutie r2@comca
73 74 2e 6e 65 74 30 1e-17 0d 31 37 30 33 32 32 st.net0. ..170322
31 37 33 30 32 33 5a 17-0d 31 39 30 33 32 32 31 173023Z. .1903221
37 33 30 32 33 5a 30 81-81 31 20 30 1e 06 03 55 73023Z0. .1.0...U
04 0a 0c 17 49 4e 54 45-47 20 50 72 6f 63 65 73 ....INTE G.Proces
73 20 47 72 6f 75 70 20-49 6e 63 31 17 30 15 06 s.Group. Inc1.0..
03 55 04 0b 0c 0e 4a 4e-49 4f 52 20 43 6f 6e 74 .U....JN IOR.Cont
72 6f 6c 73 31 1d 30 1b-06 03 55 04 03 0c 14 68 rols1.0. ..U....h
6f 6e 65 79 70 6f 74 2e-69 6e 74 65 67 70 67 2e oneypot. integpg.
63 6f 6d 31 25 30 23 06-09 2a 86 48 86 f7 0d 01 com1%0#. .*.H....
09 01 16 16 62 63 6c 6f-75 74 69 65 72 32 40 63 ....bclo utier2@c
6f 6d 63 61 73 74 2e 6e-65 74 30 81 9f 30 0d 06 omcast.n et0..0..
09 2a 86 48 86 f7 0d 01-01 01 05 00 03 81 8d 00 .*.H.... ........
30 81 89 02 81 81 00 a9-94 83 17 4b 2e bc 85 78 0....... ...K...x
ec ea 5b e9 f7 58 40 70-3b 06 ea 49 d9 33 3d 49 ..[..X@p ;..I.3=I
3d 03 5a 8d 84 db 5a b7-e5 49 1d 33 4b af 1b 59 =.Z...Z. .I.3K..Y
a3 a2 71 e2 5c 42 76 d4-10 f3 b3 c9 0e 80 1e 89 ..q.\Bv. ........
a1 62 c6 a2 82 ec 51 ab-05 cf 97 31 56 1a 95 22 .b....Q. ...1V.."
a0 b3 03 9d f7 2f a2 5b-a1 06 1e 6b bb 7a 1a a6 ...../.[ ...k.z..
b2 87 a3 14 fd db b9 e1-03 4b 45 d5 e1 ff c1 5a ........ .KE....Z
59 c4 0d 77 2d 3c da d6-14 2a 70 76 50 f1 1e bc Y..w-<.. .*pvP...
d3 0c ff 75 e6 5e 91 02-03 01 00 01 a3 70 30 6e ...u.^.. .....p0n
30 1d 06 03 55 1d 0e 04-16 04 14 29 cb 03 57 bc 0...U... ...)..W.
dd 26 e7 8a d5 e5 64 c1-d0 87 b0 3b 58 30 82 30 .&....d. ...;X0.0
0c 06 03 55 1d 13 04 05-30 03 01 01 ff 30 3f 06 ...U.... 0....0?.
03 55 1d 11 04 38 30 36-87 04 32 c5 22 4b 82 14 .U...806 ..2."K..
68 6f 6e 65 79 70 6f 74-2e 69 6e 74 65 67 70 67 honeypot .integpg
2e 63 6f 6d 82 08 68 6f-6e 65 79 70 6f 74 82 0e .com..ho neypot..
68 6f 6e 65 79 70 6f 74-5f 6a 6e 69 6f 72 30 0d honeypot _jnior0.
06 09 2a 86 48 86 f7 0d-01 01 0b 05 00 03 81 81 ..*.H... ........
00 2b 42 e0 5e 33 1a ee-b2 65 f4 da c1 18 df 73 .+B.^3.. .e.....s
e7 f5 55 d7 26 05 f6 ec-ab 67 d8 60 32 4a 7c 50 ..U.&... .g.`2J|P
56 14 c5 20 33 37 a9 8c-21 57 d8 5c 57 a7 36 b8 V...37.. !W.\W.6.
2d da 88 47 5e 93 a6 c9-fc 2c 59 83 67 8c 8d 46 -..G^... .,Y.g..F
1a 9c e7 f5 3a 27 66 db-bd 26 c0 b9 9c e1 f4 51 ....:'f. .&.....Q
4f 6b ac 3d 09 c3 30 00-bc 7e 5f 61 51 c0 ba 17 Ok.=..0. .~_aQ...
5f 29 b6 e7 3b 8e 7f eb-ae 10 99 26 9a 9a fd 70 _)..;... ...&...p
67 17 c6 7c f9 c7 f1 7e-bb 3f 8d b2 ed 43 53 c2 g..|...~ .?...CS.
d1 .
bruce_dev />
So you can see here that we receive something that looks to have the company name in it. This is the certificate and unfortunately it is in a binary ASN.1 format. That at this point is not very useful. You would have a lot of work to do if you were to parse information out of that.
So let’s see if I can help in that department.
Since in this example we attempt to connect to the HoneyPot I can separately pull its certificate in PEM format. In that form it looks like this.
bruce_dev /> cat flash/honeypot.cer
-----BEGIN CERTIFICATE-----
MIIC7TCCAlagAwIBAgIEJJmpADANBgkqhkiG9w0BAQsFADCBgTEgMB4GA1UECgwX
SU5URUcgUHJvY2VzcyBHcm91cCBJbmMxFzAVBgNVBAsMDkpOSU9SIENvbnRyb2xz
MR0wGwYDVQQDDBRob25leXBvdC5pbnRlZ3BnLmNvbTElMCMGCSqGSIb3DQEJARYW
YmNsb3V0aWVyMkBjb21jYXN0Lm5ldDAeFw0xNzAzMjIxNzMwMjNaFw0xOTAzMjIx
NzMwMjNaMIGBMSAwHgYDVQQKDBdJTlRFRyBQcm9jZXNzIEdyb3VwIEluYzEXMBUG
A1UECwwOSk5JT1IgQ29udHJvbHMxHTAbBgNVBAMMFGhvbmV5cG90LmludGVncGcu
Y29tMSUwIwYJKoZIhvcNAQkBFhZiY2xvdXRpZXIyQGNvbWNhc3QubmV0MIGfMA0G
CSqGSIb3DQEBAQUAA4GNADCBiQKBgQCplIMXSy68hXjs6lvp91hAcDsG6knZMz1J
PQNajYTbWrflSR0zS68bWaOiceJcQnbUEPOzyQ6AHomhYsaiguxRqwXPlzFWGpUi
oLMDnfcvoluhBh5ru3oaprKHoxT927nhA0tF1eH/wVpZxA13LTza1hQqcHZQ8R68
0wz/deZekQIDAQABo3AwbjAdBgNVHQ4EFgQUKcsDV7zdJueK1eVkwdCHsDtYMIIw
DAYDVR0TBAUwAwEB/zA/BgNVHREEODA2hwQyxSJLghRob25leXBvdC5pbnRlZ3Bn
LmNvbYIIaG9uZXlwb3SCDmhvbmV5cG90X2puaW9yMA0GCSqGSIb3DQEBCwUAA4GB
ACtC4F4zGu6yZfTawRjfc+f1VdcmBfbsq2fYYDJKfFBWFMUgMzepjCFX2FxXpza4
LdqIR16Tpsn8LFmDZ4yNRhqc5/U6J2bbvSbAuZzh9FFPa6w9CcMwALx+X2FRwLoX
Xym25zuOf+uuEJkmmpr9cGcXxnz5x/F+uz+Nsu1DU8LR
-----END CERTIFICATE-----
bruce_dev />
There is a nice option in the CERTMGR command to dump that in some meaningful form.
bruce_dev /> certmgr -d flash/honeypot.cer
0000 30 82 02 ED SEQUENCE { (749 bytes)
0004 30 82 02 56 | SEQUENCE { (598 bytes)
0008 A0 03 | | [0] EXPLICIT { (3 bytes)
000A 02 01 | | | INTEGER 02
| | }
000D 02 04 | | INTEGER 2499A900
0013 30 0D | | SEQUENCE { (13 bytes)
0015 06 09 | | | OBJECT IDENTIFIER 1.2.840.113549.1.1.11
0020 05 00 | | | NULL
| | }
0022 30 81 81 | | SEQUENCE { (129 bytes)
0025 31 20 | | | SET { (32 bytes)
0027 30 1E | | | | SEQUENCE { (30 bytes)
0029 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.10
002E 0C 17 | | | | | UTF8STRING 'INTEG Process Group Inc'
| | | | }
| | | }
0047 31 17 | | | SET { (23 bytes)
0049 30 15 | | | | SEQUENCE { (21 bytes)
004B 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.11
0050 0C 0E | | | | | UTF8STRING 'JNIOR Controls'
| | | | }
| | | }
0060 31 1D | | | SET { (29 bytes)
0062 30 1B | | | | SEQUENCE { (27 bytes)
0064 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.3
0069 0C 14 | | | | | UTF8STRING 'honeypot.integpg.com'
| | | | }
| | | }
007F 31 25 | | | SET { (37 bytes)
0081 30 23 | | | | SEQUENCE { (35 bytes)
0083 06 09 | | | | | OBJECT IDENTIFIER 1.2.840.113549.1.9.1
008E 16 16 | | | | | IA5STRING 'bcloutier2@comcast.net'
| | | | }
| | | }
| | }
00A6 30 1E | | SEQUENCE { (30 bytes)
00A8 17 0D | | | UTCTIME[13] 170322173023Z
00B7 17 0D | | | UTCTIME[13] 190322173023Z
| | }
00C6 30 81 81 | | SEQUENCE { (129 bytes)
00C9 31 20 | | | SET { (32 bytes)
00CB 30 1E | | | | SEQUENCE { (30 bytes)
00CD 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.10
00D2 0C 17 | | | | | UTF8STRING 'INTEG Process Group Inc'
| | | | }
| | | }
00EB 31 17 | | | SET { (23 bytes)
00ED 30 15 | | | | SEQUENCE { (21 bytes)
00EF 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.11
00F4 0C 0E | | | | | UTF8STRING 'JNIOR Controls'
| | | | }
| | | }
0104 31 1D | | | SET { (29 bytes)
0106 30 1B | | | | SEQUENCE { (27 bytes)
0108 06 03 | | | | | OBJECT IDENTIFIER 2.5.4.3
010D 0C 14 | | | | | UTF8STRING 'honeypot.integpg.com'
| | | | }
| | | }
0123 31 25 | | | SET { (37 bytes)
0125 30 23 | | | | SEQUENCE { (35 bytes)
0127 06 09 | | | | | OBJECT IDENTIFIER 1.2.840.113549.1.9.1
0132 16 16 | | | | | IA5STRING 'bcloutier2@comcast.net'
| | | | }
| | | }
| | }
014A 30 81 9F | | SEQUENCE { (159 bytes)
014D 30 0D | | | SEQUENCE { (13 bytes)
014F 06 09 | | | | OBJECT IDENTIFIER 1.2.840.113549.1.1.1
015A 05 00 | | | | NULL
| | | }
015C 03 81 8D | | | BITSTRING[140] Encapsulates {
0000 30 81 89 | | | | SEQUENCE { (137 bytes)
0003 02 81 81 | | | | | INTEGER
| | | | | A99483174B2EBC8578ECEA5BE9F75840703B06EA49D9333D
| | | | | 493D035A8D84DB5AB7E5491D334BAF1B59A3A271E25C4276
| | | | | D410F3B3C90E801E89A162C6A282EC51AB05CF9731561A95
| | | | | 22A0B3039DF72FA25BA1061E6BBB7A1AA6B287A314FDDBB9
| | | | | E1034B45D5E1FFC15A59C40D772D3CDAD6142A707650F11E
| | | | | BCD30CFF75E65E91
0087 02 03 | | | | | INTEGER 010001
| | | | }
| | | }
| | }
01EC A3 70 | | [3] EXPLICIT { (112 bytes)
01EE 30 6E | | | SEQUENCE { (110 bytes)
01F0 30 1D | | | | SEQUENCE { (29 bytes)
01F2 06 03 | | | | | OBJECT IDENTIFIER 2.5.29.14
01F7 04 16 | | | | | OCTETSTRING[22] Encapsulates {
0000 04 14 | | | | | | OCTETSTRING[20]
| | | | | | 29CB0357BCDD26E78AD5E564C1D087B0 )..W..&....d....
| | | | | | 3B583082 ;X0.
| | | | | }
| | | | }
020F 30 0C | | | | SEQUENCE { (12 bytes)
0211 06 03 | | | | | OBJECT IDENTIFIER 2.5.29.19
0216 04 05 | | | | | OCTETSTRING[5] Encapsulates {
0000 30 03 | | | | | | SEQUENCE { (3 bytes)
0002 01 01 | | | | | | | BOOLEAN TRUE(255)
| | | | | | }
| | | | | }
| | | | }
021D 30 3F | | | | SEQUENCE { (63 bytes)
021F 06 03 | | | | | OBJECT IDENTIFIER 2.5.29.17
0224 04 38 | | | | | OCTETSTRING[56] Encapsulates {
0000 30 36 | | | | | | SEQUENCE { (54 bytes)
0002 87 04 | | | | | | | [7] 32C5224B 2."K
0008 82 14 | | | | | | | [2]
| | | | | | | 686F6E6579706F742E696E7465677067 honeypot.integpg
| | | | | | | 2E636F6D .com
001E 82 08 | | | | | | | [2] 686F6E6579706F74 honeypot
0028 82 0E | | | | | | | [2] 686F6E6579706F745F6A6E696F72 honeypot_jnior
| | | | | | }
| | | | | }
| | | | }
| | | }
| | }
| }
025E 30 0D | SEQUENCE { (13 bytes)
0260 06 09 | | OBJECT IDENTIFIER 1.2.840.113549.1.1.11
026B 05 00 | | NULL
| }
026D 03 81 81 | BITSTRING[128] 0 unused bits
| 2B42E05E331AEEB265F4DAC118DF73E7 +B.^3...e.....s.
| F555D72605F6ECAB67D860324A7C5056 .U.&....g.`2J|PV
| 14C5203337A98C2157D85C57A736B82D .. 37..!W.\W.6.-
| DA88475E93A6C9FC2C5983678C8D461A ..G^....,Y.g..F.
| 9CE7F53A2766DBBD26C0B99CE1F4514F ...:'f..&.....QO
| 6BAC3D09C33000BC7E5F6151C0BA175F k.=..0..~_aQ..._
| 29B6E73B8E7FEBAE1099269A9AFD7067 )..;......&...pg
| 17C67CF9C7F17EBB3F8DB2ED4353C2D1 ..|...~.?...CS..
}
bruce_dev />
Uh, This is still likely quite cryptic for your use. ASN.1 is fun. You might notice the hexadecimal in this dump follows that dumped by our application in the prior post. This demonstrates the inherent structure in the ASN.1 Certificate Format.
So if I am going to be of any help there is more work to be done.
After thinking about some kind of conversion from ASN.1 to JSON I have decided to stick with ASN.1 for this purpose. I’ll develop an ASN1 class that will help with parsing. The reason to hang with ASN.1 is that you will be able to confirm signatures.
That reminds me too that, I should write something about Signing. Since you now have access to RSA cryptography…
Alright. A couple of posts back we extracted the certificate from our secure connection. I dumped it in binary and also using CERTMGR to see the ASN.1 structure.
First of all the certificate is delivered in DER format. This defines the binary encoding used to transfer the signed certificate and that we see in the dump. A standard ASN.1 definition for a signed certificate is compiled into DER. The format defined for these certificates is x509 which is defined in RFC 5280. You may also need information contained in RFC 5246 which is the latest for TLSv1.2.
Okay so that is a lot of work and if you have to read all of that then forget it, right? Let me try to gloss over it and drive to doing something meaningful with this binary certificate stuff.
I have started to pull together an Asn1 class which will help us work with the DER encoded binary data. It was apparent from the CERTMGR dump that there is some structure to it. I’ll try to vaguely describe that from the top down.
First notice that the whole signed certificate as obtained from the connection is enclosed in a SEQUENCE. That is an ASN.1 object which in DER has a tag (ASN_SEQUENCE), a length, and data or content. From the RFCs we expect the following structure.
Certificate ::= SEQUENCE {
tbsCertificate TBSCertificate,
signatureAlgorithm AlgorithmIdentifier,
signatureValue BIT STRING }
So the top SEQUENCE contains three objects. Here “TBS” stands for To Be Signed. So the tbsCertificate is the Certificate to be signed or that has been signed. It is information that by itself is a SEQUENCE of objects. The signatureAlgorithm defines the procedure used in the signing. That is a SEQUENCE too with some objects within. And, the signatureValue turns out to be some tacked on bit data in a BITSTRING. That we will see is the actual signature.
So let’s modify our little program that gets the target host’s certificate to use my prototype Asn1 class. We will first confirm that the initial SEQUENCE covers all of the signed certificate and then itemize its content.
package jtest;
import com.integpg.system.Debug;
import java.net.Socket;
public class Main {
public static void main(String[] args) throws Exception {
// Establish a Secure Socket, get streams, and set a timeout
Socket dataSocket = new Socket("50.197.34.75", 443);
dataSocket.setSecure(true);
// Obtain the certificate
byte[] cert;
while ((cert = dataSocket.getCertificate()).length == 0)
System.sleep(100);
dataSocket.close();
// analyze
Asn1 asn = new Asn1(cert);
// details about the object
System.out.println("Overall Signed Certificate Length: " + cert.length);
System.out.println("ASN.1 Object tag: " + asn.getTag());
System.out.printf("ASN.1 Object flags: 0x%02x\n", asn.getFlags());
System.out.println("ASN.1 Object content size: " + asn.getLength());
// skip the object and check for more data (should be only 1 object)
asn.skip();
if (!asn.hasMoreData())
System.out.println("Signed Certificate is a sigle object as expected");
else
System.out.println("Something is wrong!");
}
}
bruce_dev /> jtest
Overall Signed Certificate Length: 753
ASN.1 Object tag: 16
ASN.1 Object flags: 0x20
ASN.1 Object content size: 749
Signed Certificate is a sigle object as expected
bruce_dev />
This demonstrates that the SEQUENCE object contains the entire signed certificate. 753 bytes were delivered and aside from the 4-byte header (tag and length) the content covers the rest of the data. The tag of 16 tells us it is a SEQUENCE and the flag 0x20 tells us it is a CONSTRUCT.
Here are tags and flags that I have defined in the Asn1 class.
static public final int ASN_BOOLEAN = 1;
static public final int ASN_INTEGER = 2;
static public final int ASN_BITSTRING = 3;
static public final int ASN_OCTETSTRING = 4;
static public final int ASN_NULL = 5;
static public final int ASN_OBJECTID = 6;
static public final int ASN_OBJECTDESC = 7;
static public final int ASN_INSTANCEOF = 8;
static public final int ASN_REAL = 9;
static public final int ASN_ENUM = 10;
static public final int ASN_EMBEDDED = 11;
static public final int ASN_UTF8STRING = 12;
static public final int ASN_RELATIVEOID = 13;
static public final int ASN_SEQUENCE = 16;
static public final int ASN_SET = 17;
static public final int ASN_NUMERIC = 18;
static public final int ASN_PRINTABLE = 19;
static public final int ASN_T61 = 20;
static public final int ASN_VIDEOTEX = 21;
static public final int ASN_IA5STRING = 22;
static public final int ASN_UTCTIME = 23;
static public final int ASN_GENTIME = 24;
static public final int ASN_GRAPHIC = 25;
static public final int ASN_VISIBLESTR = 26;
static public final int ASN_GENSTRING = 27;
static public final int ASN_UNIVSTRING = 28;
static public final int ASN_CHARSTR = 29;
static public final int ASN_BMPSTR = 30;
static public final int ASN_HIGHFORM = 31;
static public final int ASN_CONSTRUCT = 0x20;
static public final int ASN_APPLICATION = 0x40;
static public final int ASN_CONTEXT = 0x80;
static public final int ASN_PRIVATE = 0xC0;
So let’s look into the overall SEQUENCE and see that those three objects are to be found. We’ll just list the tags for the objects we find. Her are the changes to our test program.
// analyze
Asn1 asn = new Asn1(cert);
// descend into the SEQUENCE object and itemize the objects it contains.
asn.descend();
while (asn.hasMoreData()) {
System.out.println("ASN.1 Object tag: " + asn.getTag());
System.out.println("ASN.1 Object length: " + asn.getLength());
System.out.println("");
asn.skip();
}
bruce_dev /> jtest
ASN.1 Object tag: 16
ASN.1 Object length: 598
ASN.1 Object tag: 16
ASN.1 Object length: 13
ASN.1 Object tag: 3
ASN.1 Object length: 129
bruce_dev />
So there are three parts. Two SEQUENCEs and a BITSTRING. Those correspond to tbsCertificate, signatureAlgorithm and signatureVauerespectively which is what is expected.
Certificate ::= SEQUENCE {
tbsCertificate TBSCertificate,
signatureAlgorithm AlgorithmIdentifier,
signatureValue BIT STRING }
Let’s extract the key parts of this signed certificate and dump the signatureValue.
// analyze
Asn1 asn = new Asn1(cert);
asn.descend();
// obtain the certificate
Asn1 tbsCertificate = new Asn1(asn.getData());
asn.skip();
Asn1 signatureAlgorithm = new Asn1(asn.getData());
asn.skip();
byte[] bitstring = asn.getData();
// remove leading unused bit count supplied with BITSTRING
byte[] signatureValue = new byte[bitstring.length - 1];
ArrayUtils.arraycopy(bitstring, 1, signatureValue, 0, signatureValue.length);
// dump the signature
Debug.dump(signatureValue);
bruce_dev /> jtest
2b 42 e0 5e 33 1a ee b2-65 f4 da c1 18 df 73 e7 +B.^3... e.....s.
f5 55 d7 26 05 f6 ec ab-67 d8 60 32 4a 7c 50 56 .U.&.... g.`2J|PV
14 c5 20 33 37 a9 8c 21-57 d8 5c 57 a7 36 b8 2d ...37..! W.\W.6.-
da 88 47 5e 93 a6 c9 fc-2c 59 83 67 8c 8d 46 1a ..G^.... ,Y.g..F.
9c e7 f5 3a 27 66 db bd-26 c0 b9 9c e1 f4 51 4f ...:'f.. &.....QO
6b ac 3d 09 c3 30 00 bc-7e 5f 61 51 c0 ba 17 5f k.=..0.. ~_aQ..._
29 b6 e7 3b 8e 7f eb ae-10 99 26 9a 9a fd 70 67 )..;.... ..&...pg
17 c6 7c f9 c7 f1 7e bb-3f 8d b2 ed 43 53 c2 d1 ..|...~. ?...CS..
bruce_dev />
We see from the CERTMGR dump a few posts back that this is correct.
How can we check the signature?
To start since I know this is from our HoneyPot unit I will grab the public key directly from the JNIOR. I’ll save this in a pubkey.pem file. Since this is a self-signed certificate this public key is already in the tbsCertificate but to avoid the complexity of digging in to get it we’ll start with a handy copy of the key. We can also tell that this certificate’s signature was done with RSA encryption and the SHA256 or SHA2 hash. There are other signature algorithms. This is the one that the JNIOR used. So to keep it simple we’ll just work with that right now.
The Certificate Signing procedure is “simple”. When the certificate was signed the JNIOR
- computed the SHA256 hash over the ASN.1 DER encoded tbsCertificate object
- built a simple ASN.1 structure defining the algorithm with an OID and storing the hash as an OCTET STRING
- encrypted the DER encoded hash value using the JNIOR’s RSA Private Key
- appended the signingAlgorithm information and the signatureValue to the tbsCertificate creating the signed certificate.
So to verify the Signed Certificate we can reverse the process. So we will do the following:
- extract the tbsCertificate ASN.1 DER encoding from the signed certificate
- calculate the SHA256 over the tbsCertificate block
- obtain the BIT STRING appended to the signed certificate
- decrypt the BIT String using the JNIOR’s RSA Public Key
- look into the resulting ASN.1 structure for the stored copy of the hash
- if our calculated hash matches that stored then the certificate verifies
// analyze
Asn1 asn = new Asn1(cert);
asn.descend();
// obtain the certificate
byte[] tbsCertificate = asn.getObject();
asn.skip();
byte[] signatureAlgorithm = asn.getData();
asn.skip();
byte[] bitstring = asn.getData();
// remove leading unused bit count supplied with BITSTRING
byte[] signatureValue = new byte[bitstring.length - 1];
ArrayUtils.arraycopy(bitstring, 1, signatureValue, 0, signatureValue.length);
Here we parse the signed certificate to extract both the tbsCertificate and the signatureValue. Note that I used getObject() from the Asn1class to not only get the certificate content but also the header for the ASN.1 SEQUENCE. The hash includes all of it.
Next we calculate the SHA256 for the tbsCertificate block. The SHA256 methods are exposed in JANOS v1.6.3 and later.
// calculate SHA-256 on tbsCertificate and signatureAlgorithm
byte[] hash = Security.hashMessage256(tbsCertificate);
Debug.dump(hash);
System.out.println("");
bruce_dev /> jtest
db 67 e8 3b 8a 7e c1 ab-ef 76 16 0b 2b 45 e1 26 .g.;.~.. .v..+E.&
c6 fa eb 31 4a 1c d0 5f-23 b0 a7 0f 7a 03 5b e6 ...1J.._ #...z.[.
Finally we read the HoneyPot’s public key from the file and perform the RSA decryption. This dumps the decrypted BIT STRING content.
// fetch the HoneyPot public key
File keyfile = new File("/flash/pubkey.pem");
DataInputStream fin = new DataInputStream(new FileInputStream(keyfile));
byte[] pubkey = new byte[fin.available()];
fin.readFully(pubkey);
fin.close();
byte[] sig = Security.decrypt(signatureValue, 0, pubkey, 0);
Debug.dump(sig);
bruce_dev /> jtest
db 67 e8 3b 8a 7e c1 ab-ef 76 16 0b 2b 45 e1 26 .g.;.~.. .v..+E.&
c6 fa eb 31 4a 1c d0 5f-23 b0 a7 0f 7a 03 5b e6 ...1J.._ #...z.[.
30 31 30 0d 06 09 60 86-48 01 65 03 04 02 01 05 010...`. H.e.....
00 04 20 db 67 e8 3b 8a-7e c1 ab ef 76 16 0b 2b ....g.;. ~...v..+
45 e1 26 c6 fa eb 31 4a-1c d0 5f 23 b0 a7 0f 7a E.&...1J .._#...z
03 5b e6 .[.
bruce_dev />
If the public key properly decrypts the signingValue you will see a valid ASN.1 DER encoded structure. Manually we see that it starts with a SEQUENCE and the length is 49 bytes. In that SEQUENCE there is another of just 13 bytes. That contains the OID. After that there is a 32 byte OCTET STRING containing the hash.
So just by eye we see that the last 32 bytes of the decrypted signingValue do match the calculated SHA256 hash. We have verified the signature!
One of the parts of the tbsCertificate defines the Issuer and the other the Subject of the certificate. Since the JNIOR creates a self-signed certificate the Issuer and Subject are the same.
If you look back to the CERTMGR dump of the certificate you see that INTEG Process Group Inc appears twice. The first is for the Issuer and the second the Subject. There is a SEQUENCE following that which contains a BIT STRING that encapsulates two INTEGERs. That is the Subject’s RSA Public Key. That would match the HoneyPot’s Public Key. We could have gone into the certificate for that key. But that works ONLY for a self-signed certificate like this.
More generally the Issuer signs the Certificate using the Issuer’s RSA Private (and highly secret) Key and the Issuer is not the same as the Subject. In that case the Issuer’s RSA Public Key is NOT in the certificate. We would need to find an independent source for the key. Windows, for instance, looks to the Trusted Root Certificate Authorities store for another certificate, one for the Issuer where the public key can be found.
It can even be more complex as there might be a chain of trust. If the certificate is signed by an Issuer that is likely not to be found in the system’s certificate store then an additional one or more certificates might be transmitted during TLS negotiation. We would have to follow the chain verifying each certificate until we reached a trusted certificate from the system’s store or otherwise.
The JNIOR does not contain a specific trusted certificate store for this purpose. If we were to be verifying certificates in this way we would need to create something or otherwise rely on a remote system.